Netskope is a leading provider of cloud security with its security service edge, single-pass architecture. Using clients to steer traffic to the Internet through the Netskope Security Cloud means that customers can securely enable data moving into and out of the distributed corporate environment. But this traffic has to originate from an endpoint—and endpoints can be compromised. How do organizations know whether SaaS traffic originating from an endpoint is potentially compromised or at risk? Here’s how a new integration between Netskope and Tanium can help.
Netskope has chosen to partner with Tanium, a platform that provides IT and security leaders visibility and control across all endpoints in on-premises, cloud, and hybrid environments. Trusted by nearly half of the Fortune 100 and multiple branches of the U.S. Armed Forces, their approach delivers accurate, complete, and up-to-date endpoint data. Tanium’s platform provides IT asset inventory management capabilities combined with a suite of other patching and compliance tools to ensure that assets are correctly provisioned, maintained, and managed. Tanium can examine endpoint posture to an astonishing degree, surfacing deployed vulnerability patches (or their absence), software levels, and brands (or their absence) running or just installed, just to name a few examples.
The integration between Netskope and Tanium enables joint customers to leverage Tanium’s high-fidelity endpoint data and user-friendly natural language search capabilities to determine if an endpoint’s overall posture equates to “compliant,” “safe,” or “managed.” These endpoint posture dispositions, determined either one-time or on a recurring basis, would drive a decision to have Netskope treat that endpoint differently than a non-compliant, risky, or unmanaged device. Utilizing adaptive policy controls, the user of that non-compliant device may not be able to download or upload files while the device is in a “risky” posture, but can still perform basic functions–such as browsing the web, sending email, etc.
Once Tanium finds the device to be compliant again, it can flag the endpoint enabling Netskope to determine its new state, match against the compliant policy, and—in this example—let the user again move files around, knowing that the USER is making those decisions, not a potentially compromised host.
Of course, users can’t benefit from Netskope’s protection capabilities if it isn’t deployed or up-to-date. Leveraging Tanium’s software management and configuration management capabilities, IT leaders can ensure that the latest Netskope steering client is deployed, installed, and active on managed hosts.
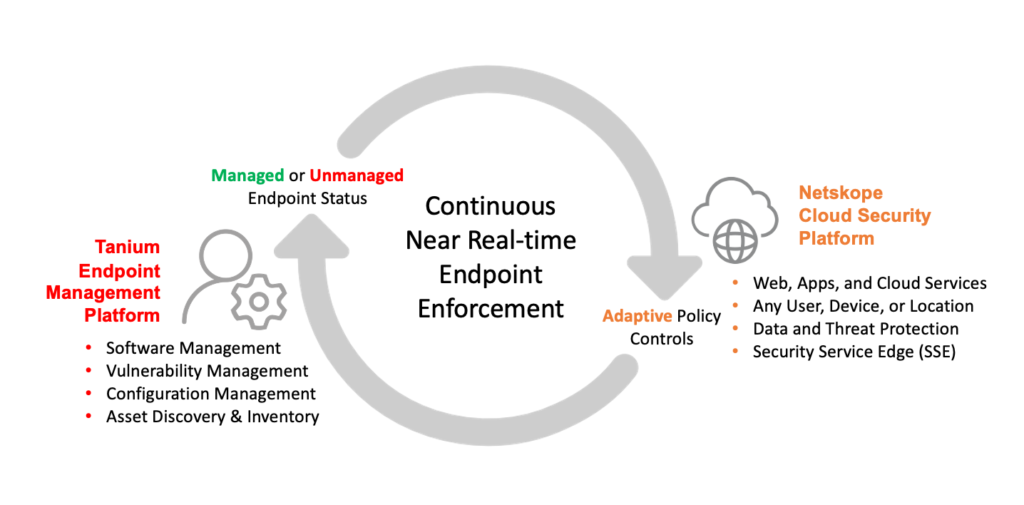
Joint customers can leverage this integration and relationship to drive a continuous near real-time endpoint enforcement approach to access web, apps, and cloud resources, giving Netskope a key additional piece of context in adaptive policy controls to map users’ cloud and data activities to their level of risk. This is the power of the Netskope Security Cloud’s leading SSE solution for SASE architecture integration with Tanium, the only platform that provides complete, accurate, and high-fidelity endpoint data trusted by the most demanding and complex organizations in the world.
Click here to see a demo of the Netskope and Tanium integration in action. Contact [email protected] to try out the Netskope integration in your Tanium environment.




 Retour
Retour 





















 Lire le blog
Lire le blog